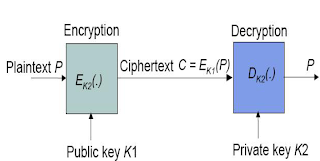
v A cryptographic system that uses two keys -- a public key known
to everyone and a private or secret key known only to the
recipient of the message.
v When John wants to send a secure message to Jane, he uses Jane's
public key to encrypt the message. Jane then uses her private key to decrypt
it.
v An important element to the public key system is that the public
and private keys are related in such a way that only the public key can be used
to encrypt messages and only the corresponding private key can be used to
decrypt them. Moreover, it is virtually impossible to deduce the private key if
you know the public key.
v Public key cryptography was invented in 1976 by Whitfield Diffie
and Martin Hellman. For this reason, it is sometime called Diffie-Hellman
encryption.
v It is also called asymmetric encryption because it uses two
keys instead of one key (symmetric encryption).
One important
requirement for public key cryptography is that it must not be possible to
determine K2 from K1.
Example : RSA
(Rivest Shamir and Adleman ) Algorithm ;
Public key
cryptography developed to address two key issues:
– key
distribution – how to have secure communications in general without having to
trust a KDC with your key
– digital
signatures – how to verify a message comes intact from the claimed sender
Key Distribution
center (KDC)
Secret key
systems require every pair of users to share a separate key.
Consequently the
number of keys grow as the square of the number of users making these systems
unfeasible for large scale use.
This problem can
be addresses through the introduction of KDC
For example,
assume the KDC shares a different secret key with each user. Han Solo contacts
the KDC with a request to communicate with Luke Skywalker (1). The KDC creates a
symmetric secret session key, encrypts it with the secret key shared with Han
(2) and transmits the key to Han (3). Next the KDC encrypts the secret session
key with the secret key shared with Luke (2), then transmits the message to
Luke (3). Luke and Han now have the secret session key and commence the
communication. Note that changing session keys enhances the security of the
communications. The message from the KDC to Luke and Han
will normally
specify the algorithm (including padding scheme, etceteras) in addition to the session
key.
Certification
Authority (CA)
• Public key
systems require only one pair of keys per user, but they still face the problem
of how public key are to be distributed.
• The public
keys must be certified somehow.
• One approach
to address this problem is to establish a Certification Authority (CA).
• To issue
certificates that consist of signed message stating the name of given user, his
or her public key, s serial number identifying the certificate and an expiration
date








0 comments